aws
Friday, July 22, 2016
Monday, July 18, 2016
Architecting for the Cloud: AWS Best Practices
Migrating applications to AWS, even without significant changes (an approach known as “lift and shift”).
Architect in a such a way to exploit the elasticity of cloud.
The Cloud Computing Difference:
1. IT Assets Become Programmable Resources
2. Global, Available, and Unlimited Capacity
3. Higher Level Managed Services : EC2, storage, database, analytics, application, and deployment services
4. Security Built In : The AWS cloud provides governance capabilities that enable continuous monitoring of configuration changes to your IT resources. Since AWS assets are programmable resources, your security policy can be formalized and embedded with the design of your infrastructure.
6. Design Principles
7. Scalability : Architecture can support growth in users, traffic, or data size with no drop in performance.
While cloud computing provides virtually unlimited on-demand capacity, your design needs to be able to take advantage of those resources seamlessly.
A. Scaling Vertically : On Amazon EC2, this can easily be achieved by stopping an instance and resizing it to an instance type that has more RAM, CPU, IO, or networking capabilities.
B. Scaling Horizontally: Increase in the number of resources.Not all architectures are designed to distribute their workload to multiple resources.
Stateless Applications: A stateless application is an application that needs no knowledge of previous interactions and stores no session.
How to distribute load to multiple nodes:
Push Model:
Elastic Load Balancer (ELB) routing requests to EC2.
Aletnerate approach DNS round robin (e.g., with Amazon Route 53): Round robin fashion. While easy to implement, this approach does not always work well with the elasticity of cloud computing. This is because even if you can set low time to live (TTL) values for your DNS records, caching DNS resolvers are outside the control of Amazon Route 53 and might not always respect your settings.
Pull Model:
Data that need to be processed could be stored as messages in a queue using Amazon Simple Queue Service (Amazon SQS) or as a streaming data solution like Amazon Kinesis.
Stateless Components:Use HTTP cookies to store information about a session at the client’s browser (e.g., items in the shopping cart).
Two drawbacks
1.Content of the HTTP cookies can be tampered with
2. Second, HTTP cookies are transmitted with every request ( Keep their size to minimum)
A common solution to this problem is to store user session information in a database. Amazon DynamoDB is a great choice due to its scalability, high availability, and durability characteristics.
Amazon S3 for large file storage.
Amazon Simple Workflow Service (Amazon SWF) can be utilized to centrally store execution history and make these workloads stateless.
Stateful Components:
Databases are stateful
Many legacy applications were designed to run on a single server by relying on local compute resources.
Other use cases might require client devices to maintain a connection to a specific server for prolonged periods of time. e.g. Consistent view of the
game in real time multiplayer game. Session affinity.
How to implement session affinity:
For HTTP/S traffic, session affinity can be achieved through the “sticky sessions” feature of ELB4. Elastic Load Balancing will attempt to use the same server for that user for the duration of the session.
DNS
Clinet API to discover information (server)
Distributed Processing:
By dividing a task and its data into many small fragments of work, you can execute each of them in any of a larger set of available compute resources.
How to implement distributed processing.
Offline batch jobs can be horizontally scaled by using a distributed data processing engine like Apache Hadoop. On AWS, you can use the Amazon Elastic MapReduce (Amazon EMR) service to run Hadoop workloads on top of a fleet of EC2 instances without the operational complexity.
For real-time processing of streaming data, Amazon Kinesis partitions data in multiple shards that can then be consumed by multiple Amazon EC2 or AWS Lambda resources to achieve scalability.
Disposable Resources Instead of Fixed Servers:
Fixed resources:
Manual efforts and Cost
Configuration drift - Changes and software patches applied through time can result in untested and heterogeneous configurations across different environments.
Instantiating Compute Resources:
There are a few approaches on how to achieve an automated and repeatable process.
Bootstrapping -
Start with a default configuration. You can then execute automated bootstrapping actions.
Parameterize configuration details that vary between different environments (e.g., production, test, etc.)
Bootstrapping in practice
You can use user data scripts and cloud-init6 directives or AWS OpsWorks lifecycle events7 to automatically set up new EC2 instances.
You can use simple scripts, configuration management tools like Chef or Puppet.
AWS OpsWorks natively supports Chef recipes or Bash/PowerShell scripts.
In addition, through custom scripts and the AWS APIs, or
through the use of AWS CloudFormation support for AWS Lambda-backed custom resources, it is possible to write provisioning logic that acts on almost any AWS resource.
Golden Images
Amazon EC2 instances, Amazon RDS DB instances, Amazon Elastic Block Store (Amazon EBS) volumes, etc., can be launched from a golden image: a snapshot of a particular state of that resource.
Compared to bootstrapping faster.
Create AMI.
Versioning of AMI's.
Containers:
Docker - Docker Image, which is a standardized unit for software development, containing everything the software needs to run: code, runtime, system tools, system libraries, etc. AWS Elastic Beanstalk and the Amazon EC2 Container Service (Amazon ECS) support Docker and enable you to deploy and manage multiple Docker containers across a cluster of Amazon EC2 instances.
Hybrid:
Some part in Golden Image, some part in bootstrapping
The line between bootstrapping and golden image:
Items that do not change often or that introduce external dependencies will typically be part of your golden image.
For example, web server software
Items that change often or differ between your various environments can be set up dynamically through bootstrapping actions.
For example, if you are deploying new versions of your application frequently
Database hostname configuration (different between the test and production environments)
User data or tags.
AWS Elastic Beanstalk follows the hybrid model.
It provides preconfigured run time environments (each initiated from its own AMI10)
but allows you to run bootstrap actions (through configuration files called .ebextensions11) and configure environmental variables to parameterize the environment differences.
Infrastructure as Code:
Apply techniques, practices, and tools from software development to make your whole infrastructure reusable, maintainable, extensible, and testable.
- Create and manage - AWS resources, and
- provision and update them in an orderly and predictable fashion.
- Describe the AWS resources, and any associated dependencies or run time parameters, required to run your application.
- Version control repository, allowing architectures to be reused and production environments to be reliably cloned for testing.
Automation:
AWS Elastic Beanstalk : Developers can simply upload their application code and the service automatically handles all the details
Amazon EC2 Auto recovery: Recovered instance is identical to the original instance, including the instance ID, private IP addresses, Elastic IP addresses, and all instance metadata ( Only certain EC2 Type). During instance recovery memory data is lost.
Auto Scaling:
Amazon CloudWatch Alarms: Sends an Amazon Simple Notification Service (Amazon SNS) message -
SNS Message automatically trigger AWS Lambda function,
enqueue message to SQS or
POST request to an HTTP/S endpoint.
Amazon CloudWatch Events:
AWS OpsWorks Lifecycle events:
AWS OpsWorks supports continuous configuration through lifecycle events that automatically update your instances’ configuration to adapt to environment changes. These events can be used to trigger Chef recipes on each instance to perform specific configuration tasks. For example, when a new instance is successfully added to a Database server layer, the configure event could trigger a Chef recipe that updates the Application server layer configuration to point to the new database instance.
AWS Lambda Scheduled events:
Saturday, July 2, 2016
AWS Security In your VPC
Amazon VPC provides three features that you can use to increase and monitor the security for your VPC:
• Security groups — Act as a firewall for associated Amazon EC2 instances, controlling both inbound and outbound traffic at the instance level
• Network access control lists (ACLs) — Act as a firewall for associated subnets, controlling both inbound and outbound traffic at the subnet level
• Flow logs — Capture information about the IP traffic going to and from network interfaces in your VPC
You can monitor the accepted and rejected IP traffic going to and from your instances by creating a flow log for a VPC, subnet, or individual network interface. Flow log data is published to CloudWatch Logs, and can help you diagnose overly restrictive or overly permissive security group and network ACL rules.
Amazon security groups and network ACLs don't filter traffic to or from link-local addresses
(169.254.0.0/16) or AWS-reserved addresses (the first four IP addresses and the last one in each
subnet). Similarly, flow logs do not capture IP traffic to or from these addresses.
These addresses support the services:
Domain Name Services (DNS),
Dynamic Host Configuration Protocol (DHCP),
Amazon EC2 instance metadata,
, Key Management Server (KMS—license management for Windows instances), and
routing in the subnet.
You can implement additional firewall solutions in your instances to block network communication with link-local addresses.
Comparison of Security Groups and Network ACLs:
64#
Security Groups for Your VPC:
A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign the instance to up to five security groups. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC could be assigned to a different set of security groups. If you don't specify a particular group at launch time, the instance is automatically assigned to the default security group for the VPC.
For each security group, you add rules that control the inbound traffic to instances, and a separate set of rules that control the outbound traffic.
You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC.
65#
Security Group Basics
The following are the basic characteristics of security groups for your VPC:
• You can create up to 500 security groups per VPC.You can add up to 50 rules to each security group, and associate up to 5 security groups per network interface.
• You can specify allow rules, but not deny rules.
• You can specify separate rules for inbound and outbound traffic.
• By default, no inbound traffic is allowed until you add inbound rules to the security group.
• By default, an outbound rule allows all outbound traffic.You can remove the rule and add outbound rules that allow specific outbound traffic only.
• Security groups are stateful — responses to allowed inbound traffic are allowed to flow outbound
regardless of outbound rules, and vice versa. For more information, see Connection Tracking in the
Amazon EC2 User Guide for Linux Instances.
• Instances associated with a security group can't talk to each other unless you add rules allowing it
(exception: the default security group has these rules by default).
• Security groups are associated with network interfaces. After you launch an instance, you can change the security groups associated with the instance, which changes the security groups associated with the primary network interface (eth0).You can also change the security groups associated with any other network interface. For more information about network interfaces, see Elastic Network Interfaces (ENI).
Default Security Group for Your VPC
The following table describes the default rules for a default security group.
You can change the rules for the default security group. You can't delete a default security group.
• Security groups — Act as a firewall for associated Amazon EC2 instances, controlling both inbound and outbound traffic at the instance level
• Network access control lists (ACLs) — Act as a firewall for associated subnets, controlling both inbound and outbound traffic at the subnet level
• Flow logs — Capture information about the IP traffic going to and from network interfaces in your VPC
You can monitor the accepted and rejected IP traffic going to and from your instances by creating a flow log for a VPC, subnet, or individual network interface. Flow log data is published to CloudWatch Logs, and can help you diagnose overly restrictive or overly permissive security group and network ACL rules.
Amazon security groups and network ACLs don't filter traffic to or from link-local addresses
(169.254.0.0/16) or AWS-reserved addresses (the first four IP addresses and the last one in each
subnet). Similarly, flow logs do not capture IP traffic to or from these addresses.
These addresses support the services:
Domain Name Services (DNS),
Dynamic Host Configuration Protocol (DHCP),
Amazon EC2 instance metadata,
, Key Management Server (KMS—license management for Windows instances), and
routing in the subnet.
You can implement additional firewall solutions in your instances to block network communication with link-local addresses.
Comparison of Security Groups and Network ACLs:
64#
Security Groups for Your VPC:
A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign the instance to up to five security groups. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC could be assigned to a different set of security groups. If you don't specify a particular group at launch time, the instance is automatically assigned to the default security group for the VPC.
For each security group, you add rules that control the inbound traffic to instances, and a separate set of rules that control the outbound traffic.
You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC.
65#
Security Group Basics
The following are the basic characteristics of security groups for your VPC:
• You can create up to 500 security groups per VPC.You can add up to 50 rules to each security group, and associate up to 5 security groups per network interface.
• You can specify allow rules, but not deny rules.
• You can specify separate rules for inbound and outbound traffic.
• By default, no inbound traffic is allowed until you add inbound rules to the security group.
• By default, an outbound rule allows all outbound traffic.You can remove the rule and add outbound rules that allow specific outbound traffic only.
• Security groups are stateful — responses to allowed inbound traffic are allowed to flow outbound
regardless of outbound rules, and vice versa. For more information, see Connection Tracking in the
Amazon EC2 User Guide for Linux Instances.
• Instances associated with a security group can't talk to each other unless you add rules allowing it
(exception: the default security group has these rules by default).
• Security groups are associated with network interfaces. After you launch an instance, you can change the security groups associated with the instance, which changes the security groups associated with the primary network interface (eth0).You can also change the security groups associated with any other network interface. For more information about network interfaces, see Elastic Network Interfaces (ENI).
Default Security Group for Your VPC
The following table describes the default rules for a default security group.
You can change the rules for the default security group. You can't delete a default security group.
Monday, June 27, 2016
AWS Your VPC and Subnets
#48
Your VPC and Subnets
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS cloud.You can launch your AWS resources, such as Amazon EC2 instances, into your VPC. When you create a VPC, you specify the set of IP addresses for the VPC in the form of a Classless Inter-Domain Routing (CIDR) block (for example, 10.0.0.0/16).
Your New VPC:
The following diagram shows a new VPC with a default route table.
You need to add a subnet before you can launch an instance into your VPC.
49#
VPC Sizing:
You can assign a single CIDR block to a VPC. The allowed block size is between a /28 netmask and
/16 netmask. In other words, the VPC can contain from 16 to 65,536 IP addresses.You can't change
the size of a VPC after you create it. If your VPC is too small to meet your needs, create a new, larger VPC, and then migrate your instances to the new VPC.To do this, create AMIs from your running instances, and then launch replacement instances in your new, larger VPC..You can then terminate your old instances, and delete your smaller VPC.
50#
Connections with Your Local Network and OtherVPCs
You can optionally set up a connection between your VPC and your corporate or home network. If you have an IP address prefix in your VPC that overlaps with one of your networks' prefixes, any traffic to the network's prefix is dropped.
You can also create a VPC peering connection between your VPCs, or with a VPC in another AWS account. A VPC peering connection enables you to route traffic between the VPCs using private IP addresses; however, you cannot create a VPC peering connection between VPCs that have overlapping CIDR blocks.
Creating a VPC:
There are two ways to create a VPC using the Amazon VPC console: the Create VPC ( which creates only the VPC;you'd need to subsequently add subnets, gateways, and routing tables) dialog box and the VPC wizard.
51#
Deleting Your VPC:
You can delete your VPC at any time (for example, if you decide it's too small). However, you must
terminate all instances in the VPC first. When you delete a VPC using the VPC console, we delete all its components, such as subnets, security groups, network ACLs, route tables, Internet gateways, VPC peering connections, and DHCP options.
If you have a VPN connection, you don't have to delete it or the other components related to the VPN
(such as the customer gateway and virtual private gateway). If you plan to use the customer gateway
with another VPC, we recommend you keep the VPN connection and the gateways. Otherwise, your
network administrator must configure the customer gateway again after you create a new VPN connection.
Subnets in Your VPC:
You can create a VPC that spans multiple Availability Zones.After creating a VPC, you can add one or more subnets in each Availability Zone. Each subnet must reside entirely within one Availability Zone and cannot span zones. Availability Zones are distinct locations that are engineered to be isolated from failures in other Availability Zones. By launching instances in separate Availability Zones, you can protect your applications from the failure of a single location. AWS assigns a unique ID to each subnet.
52#
Your VPC with Subnets:
The following diagram shows a VPC that has been configured with subnets in multiple Availability Zones.You can optionally add an Internet gateway to enable communication over the Internet, or a virtual private network (VPN) connection to enable communication with your network, as shown in the diagram.
If a subnet's traffic is routed to an Internet gateway, the subnet is known as a public subnet. In this diagram,subnet 1 is a public subnet. If you want your instance in a public subnet to communicate with the Internet, it must have a public IP address or an Elastic IP address.
If a subnet doesn't have a route to the Internet gateway, the subnet is known as a private subnet. In this diagram, subnet 2 is a private subnet.
If a subnet doesn't have a route to the Internet gateway, but has its traffic routed to a virtual private gateway, the subnet is known as a VPN-only subnet. In this diagram, subnet 3 is a VPN-only subnet.
Note
Regardless of the type of subnet, the internal IP address range of the subnet is always private
— we do not announce the address block to the Internet.
53#
Subnet Sizing:
When you create a subnet, you specify the CIDR block for the subnet. The CIDR block of a subnet can be the same as the CIDR block for the VPC (for a single subnet in the VPC), or a subset (to enable multiple subnets). The allowed block size is between a /28 netmask and /16 netmask. If you create more than one subnet in a VPC, the CIDR blocks of the subnets must not overlap.
Calculate subnet CIDR blocks : http://www.subnet-calculator.com/cidr.php
The first four IP addresses and the last IP address in each subnet CIDR block are not available for you to use, and cannot be assigned to an instance. For example, in a subnet with CIDR block 10.0.0.0/24,
the following five IP addresses are reserved:
• 10.0.0.0: Network address.
• 10.0.0.1: Reserved by AWS for the VPC router.
• 10.0.0.2: Reserved by AWS for mapping to the Amazon-provided DNS.
• 10.0.0.3: Reserved by AWS for future use.
• 10.0.0.255: Network broadcast address.We do not support broadcast in a VPC, therefore we reserve this address.
Subnet Routing:
By design, each subnet must be associated with a route table, which specifies the allowed routes for outbound traffic leaving the subnet. Every subnet that you create is automatically associated with the main route table for the VPC.You can change the association, and you can change the contents of the main route table.
In the previous diagram, the route table associated with subnet 1 routes all traffic (0.0.0.0/0) to an
Internet gateway (for example, igw-1a2b3c4d). Because instance V1 has an Elastic IP address, it can
be reached from the Internet.
Note
The Elastic IP address or public IP address that's associated with your instance is accessed
through the Internet gateway of your VPC. Traffic that goes through a VPN connection between your instance and another network traverses a virtual private gateway, not the Internet gateway, and therefore does not access the Elastic IP address or public IP address.
The instance V2 can't reach the Internet, but can reach other instances in the VPC.You can allow an
instance in your VPC to initiate outbound connections to the Internet but prevent unsolicited inbound
connections from the Internet using a network address translation (NAT) gateway or instance. Because you can allocate a limited number of Elastic IP addresses, we recommend that you use a NAT device if you have more instances that require a static public IP address.
The route table associated with subnet 3 routes all traffic (0.0.0.0/0) to a virtual private gateway (for
example, vgw-1a2b3c4d). Instance V3 can reach computers in the corporate network over the VPN connection.
Subnet Security:
AWS provides two features that you can use to increase security in your VPC: security groups and network ACLs. Both features enable you to control the inbound and outbound traffic for your instances, but security groups work at the instance level, while network ACLs work at the subnet level. Security groups alone can meet the needs of many VPC users. However, some VPC users decide to use both security groups and network ACLs to take advantage of the additional layer of security that network ACLs provide.
By design, each subnet must be associated with a network ACL. Every subnet that you create is
automatically associated with the VPC's default network ACL.You can change the association, and you can change the contents of the default network ACL.
You can create a flow log on your VPC or subnet to capture the traffic that flows to and from the network interfaces in your VPC or subnet.You can also create a flow log on an individual network interface. Flow logs are published to CloudWatch Logs.
55#
Deleting Your Subnet: You must terminate any instances in the subnet first.
CLI Overview:
You can perform the tasks described on this page using a command line interface (CLI). For more
information, including a list of available API actions, see Accessing Amazon VPC (p. 6).
Create a VPC
• create-vpc (AWS CLI)
• ec2-create-vpc (Amazon EC2 CLI)
• New-EC2Vpc (AWS Tools for Windows PowerShell)
Create a Subnet• create-subnet (AWS CLI)
• ec2-create-subnet (Amazon EC2 CLI)
• New-EC2Subnet (AWS Tools for Windows PowerShell)
Describe a VPC
• describe-vpcs (AWS CLI)
• ec2-describe-vpcs (Amazon EC2 CLI)
Amazon Virtual Private Cloud User Guide
Deleting Your Subnet
• Get-EC2Vpc (AWS Tools for Windows PowerShell)
56#
Describe a Subnet
• describe-subnets (AWS CLI)
• ec2-describe-subnets (Amazon EC2 CLI)
• Get-EC2Subnet (AWS Tools for Windows PowerShell)
Delete a VPC
• delete-vpc (AWS CLI)
• ec2-delete-vpc (Amazon EC2 CLI)
• Remove-EC2Vpc (AWS Tools for Windows PowerShell)
Delete a Subnet
• delete-subnet (AWS CLI)
• ec2-delete-subnet (Amazon EC2 CLI)
• Remove-EC2Subnet (AWS Tools for Windows PowerShell)
Your Default VPC and Subnets
When we create a default VPC, we do the following to set it up for you:
• Create a default subnet in each Availability Zone.
• Create an Internet gateway and connect it to your default VPC.
• Create a main route table for your default VPC with a rule that sends all traffic destined for the Internet
to the Internet gateway.
• Create a default security group and associate it with your default VPC.
• Create a default network access control list (ACL) and associate it with your default VPC
• Associate the default DHCP options set for your AWS account with your default VPC.
The following figure illustrates the key components that we set up for a default VPC.
Instances that you launch into a default subnet receive both a public IP address and a private IP address.Instances in a default subnet also receive both public and private DNS hostnames. Instances that you launch into a nondefault subnet in a default VPC don't receive a public IP address or a DNS hostname. You can change your subnet's default public IP addressing behavior.
59#
Default Subnets:
The CIDR block for a default VPC is always a /16 netmask, for example, 172.31.0.0/16. This provides up to 65,536 private IP addresses. The netmask for a default subnet is always /20, which provides up to 4,096 addresses per subnet, a few of which are reserved for our use.
By default, a default subnet is a public subnet, because the main route table sends the subnet's traffic that is destined for the Internet to the Internet gateway.You can make a default subnet a private subnet by removing the route from the destination 0.0.0.0/0 to the Internet gateway. However, if you do this, any EC2 instance running in that subnet can't access the Internet.
60#
Launching an EC2 Instance into Your Default VPC:
When you launch an EC2 instance without specifying a subnet, it's automatically launched into a default subnet in your default VPC. By default, we select an Availability Zone for you and launch the instance into the corresponding subnet for that Availability Zone. Alternatively, you can select the Availability Zone for your instance by selecting its corresponding default subnet in the console, or by specifying the subnet or the Availability Zone in the CLI.
Monday, June 20, 2016
AWSFundas
** VPCNetworkAdminGuide **
Difference between Public IP and Static IP:
When you launch an EC2 instance, you recieve a Public IP address by which that instance is reachable.
Once you stop that instance and restart the you get a new Public IP for the same instance's.
So, Public IP get's changed everytime for an instance after stop/start.
To overcome with this problem, we attach an Elastic IP to an Instance which doesn't change after you stop / start the instance as many times.
Advantage of Having Elastic IP
-> It is kind of static IP for your Instance.
-> Doesn't change after stop/start.
If you have Elastic IP in your account and it's not in use, then you will be charged for it.
Ref: Vikash Jha
https://www.quora.com/Whats-the-difference-between-a-public-IP-and-an-elastic-IP-in-AWS-EC2
__________________
Internet Gateway :
Route Tables.
-----------------------------------
Route Table:
then we prioritize the routes as follows in your VPC, from most preferred to least preferred:
Difference between Public IP and Static IP:
When you launch an EC2 instance, you recieve a Public IP address by which that instance is reachable.
Once you stop that instance and restart the you get a new Public IP for the same instance's.
So, Public IP get's changed everytime for an instance after stop/start.
To overcome with this problem, we attach an Elastic IP to an Instance which doesn't change after you stop / start the instance as many times.
Advantage of Having Elastic IP
-> It is kind of static IP for your Instance.
-> Doesn't change after stop/start.
If you have Elastic IP in your account and it's not in use, then you will be charged for it.
Ref: Vikash Jha
https://www.quora.com/Whats-the-difference-between-a-public-IP-and-an-elastic-IP-in-AWS-EC2
__________________
Internet Gateway :
Route Tables.
-----------------------------------
Route Table:
then we prioritize the routes as follows in your VPC, from most preferred to least preferred:
- Local routes for the VPC
- Static routes whose targets are an Internet gateway, a virtual private gateway, a network interface, an instance ID, a VPC peering connection, or a VPC endpoint
- Any propagated routes from a VPN connection or AWS Direct Connect connection
If you have overlapping routes within a VPN connection and longest prefix match cannot be applied, then we prioritize the routes as follows in the VPN connection, from most preferred to least preferred:
- BGP propagated routes from an AWS Direct Connect connection
- Manually added static routes for a VPN connection
- BGP propagated routes from a VPN connection
Note
When you use the wizard in the console to create a VPC with a gateway, the wizard automatically updates the route tables to use the gateway. If you're using the command line tools or API to set up your VPC, you must update the route tables yourself.
=================================================
________________________________________________________________________
7
A main route table that all VPCs have by default, and a custom route table that was created by the wizard. The custom route table is associated with your subnet, which means that the routes in that table determine how the traffic for the subnet flows.If you add a new subnet to your VPC, it uses the main route table by default.
11
A security group acts as a virtual firewall to control the traffic for its associated instances.To use a security group, you add the inbound rules to control incoming traffic to the instance, and outbound rules to control the outgoing traffic from your instance. To associate a security group with an instance, you specify the security group when you launch the instance. If you add and remove rules from the security group, we apply those changes to the instances associated with the security group automatically.
Your VPC comes with a default security group. Any instance not associated with another security group during launch is associated with the default security group.
14
A public subnet — a subnet that has a route to an Internet gateway. However, the instance in your subnet also needs a public IP address to be able to communicate with the Internet. By default, an instance in a nondefault VPC is not assigned a public IP address.
18,19
An Internet gateway. This connects the VPC to the Internet and to other AWS products.
An instance with a private IP address in the subnet range (example: 10.0.0.6), which enables the
instance to communicate with other instances in the VPC, and an Elastic IP address (example:
198.51.100.2), which enables the instance to be reached from the Internet.
A route table entry that enables instances in the subnet to communicate with other instances in the VPC, and a route table entry that enables instances in the subnet to communicate directly over the Internet.
Tip
If you'd like instances in your VPC to communicate over the Internet without having to assign
each instance an Elastic IP address, you can use a NAT gateway.
Your VPC has an implied router (shown in the configuration diagram for this scenario.) For this scenario, the VPC wizard creates a route table that routes all traffic destined for an address outside the VPC to the Internet gateway, and associates this route table with the subnet. Otherwise, you'd need to create and associate the route table yourself.
The following table shows what the route table looks like for the example addresses used in the
configuration diagram for this scenario. The first row shows the entry for local routing in the VPC; this entry enables the instances in this VPC to communicate with each other.The second row shows the entry for routing all other subnet traffic to the Internet gateway, which is specified using its AWS-assigned identifier.
---------------------------------------------------------------------------------------------------------------------
19
AWS provides two features that you can use to increase security in your VPC: security groups and network ACLs. Both features enable you to control the inbound and outbound traffic for your instances, but security groups work at the instance level, while network ACLs work at the subnet level.
Security groups alone can meet the needs of many VPC users. However, some VPC users decide to use both security groups and network ACLs to take advantage of the additional layer of security that network ACLs provide.
Recommended Security Group Rules
Your VPC comes with a default security group whose initial settings allow all outbound traffic and allow all traffic between instances assigned to the security group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to the default security group for the VPC.
#20
By default, new security groups start with only an outbound rule that allows all traffic to leave the instances.You must add rules to enable any inbound traffic or to restrict the outbound traffic.
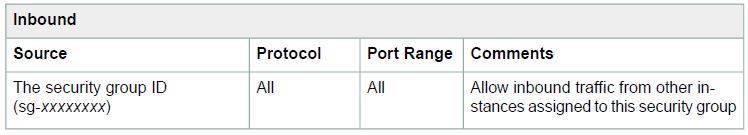
The default security group for a VPC has rules that automatically allow assigned instances to communicate with each other. To allow that type of communication between the instances in your VPC, you must add a rule like the following to your security groups.
#23
The instances in the public subnet can receive inbound traffic directly from the Internet, whereas the
instances in the private subnet can't. The instances in the public subnet can send outbound traffic directly to the Internet, whereas the instances in the private subnet can't. Instead, the instances in the private subnet can access the Internet by using a network address translation (NAT) gateway that resides in the public subnet. The database servers can connect to the Internet for software updates using the NAT gateway, but the Internet cannot initiate connections to the database servers.
Note
You can also use the VPC wizard to configure a VPC with a NAT instance; however, we
recommend that you use a NAT gateway. For more information, see NAT Gateways.
#24A NAT gateway with its own Elastic IP address. This enables instances in the private subnet to send
requests to the Internet (for example, for software updates)
A route table associated with the public subnet.This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the private subnet. The route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate with the Internet through the NAT gateway.
25#
Tip:
To help manage the instances in the private subnet, you can set up bastion servers in the public
subnet to act as proxies. For example, you can set up SSH port forwarders or RDP gateways
in the public subnet to proxy the traffic going to your database servers from your own network.
In this scenario, all traffic from each subnet that is bound for AWS (for example, to the Amazon EC2 or Amazon S3 endpoints) goes over the Internet gateway. The database servers in the private subnet can't receive traffic from the Internet directly because they don't have Elastic IP addresses. However, the database servers can send and receive Internet traffic through the NAT device in the public subnet.
Any additional subnets that you create use the main route table by default, which means that they are private subnets by default. If you'd like to make a subnet public, you can always change the route table that it's associated with.
26#
Your VPC comes with a default security group whose initial settings deny all inbound traffic, allow all outbound traffic, and allow all traffic between instances assigned to the group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to this default security group.
The instances assigned to a security group can be in different subnets.
30#
By default, instances launched into a nondefault VPC are not assigned a public IP address.
To be able to connect to your instance in the public subnet, you can assign a public IP address now,
or allocate an Elastic IP address and assign it to your instance after it's launched.To assign a publicIP address now, ensure that you choose Enable from the Auto-assign Public IP list.You do not
need to assign a public IP address to an instance in the private subnet.
Note
You can only assign a public IP address to a single, new network interface with the device
index of eth0. For more information, see Assigning a Public IP Address During Launch (p. 123).
31#
You will also require a security group for your NAT instance (NATSG), which allows the NAT instance to receive Internet-bound traffic from instances in the private subnet, as well as SSH traffic from your network. The NAT instance can also send traffic to the Internet, so that instances in the private subnet can get software updates.
33#
Scenario 3:VPC with Public and Private Subnets and Hardware VPN Access
The configuration for this scenario includes a virtual private cloud (VPC) with a public subnet and a private subnet, and a virtual private gateway to enable communication with your own network over an IPsec VPN tunnel.We recommend this scenario if you want to extend your network into the cloud and also directly access the Internet from your VPC. This scenario enables you to run a multi-tiered application with a scalable web front end in a public subnet, and to and to house your data in a private subnet that is connected to your network by an IPsec VPN connection.
34#
A VPN connection between your VPC and your network. The VPN connection consists of a virtual
private gateway located on the Amazon side of the VPN connection and a customer gateway located on your side of the VPN connection.
Instances with private IP addresses in the subnet range (examples: 10.0.0.5 and 10.0.1.5), which
enables the instances to communicate with each other and other instances in the VPC. Instances in the public subnet also have Elastic IP addresses (example: 198.51.100.1), which enables them to be
reached from the Internet. The instances can have public IP addresses assigned at launch instead of
Elastic IP addresses. Instances in the VPN-only subnet are back-end servers that don't need to accept incoming traffic from the Internet, but can send and receive traffic from your network.
A custom route table associated with the public subnet. This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the VPN-only subnet. The route table contains an entry that
enables instances in the subnet to communicate with other instances in the VPC, and an entry that
enables instances in the subnet to communicate directly with your network.
=================================================
________________________________________________________________________
7
A main route table that all VPCs have by default, and a custom route table that was created by the wizard. The custom route table is associated with your subnet, which means that the routes in that table determine how the traffic for the subnet flows.If you add a new subnet to your VPC, it uses the main route table by default.
11
A security group acts as a virtual firewall to control the traffic for its associated instances.To use a security group, you add the inbound rules to control incoming traffic to the instance, and outbound rules to control the outgoing traffic from your instance. To associate a security group with an instance, you specify the security group when you launch the instance. If you add and remove rules from the security group, we apply those changes to the instances associated with the security group automatically.
Your VPC comes with a default security group. Any instance not associated with another security group during launch is associated with the default security group.
14
A public subnet — a subnet that has a route to an Internet gateway. However, the instance in your subnet also needs a public IP address to be able to communicate with the Internet. By default, an instance in a nondefault VPC is not assigned a public IP address.
18,19
An Internet gateway. This connects the VPC to the Internet and to other AWS products.
An instance with a private IP address in the subnet range (example: 10.0.0.6), which enables the
instance to communicate with other instances in the VPC, and an Elastic IP address (example:
198.51.100.2), which enables the instance to be reached from the Internet.
A route table entry that enables instances in the subnet to communicate with other instances in the VPC, and a route table entry that enables instances in the subnet to communicate directly over the Internet.
Tip
If you'd like instances in your VPC to communicate over the Internet without having to assign
each instance an Elastic IP address, you can use a NAT gateway.
Your VPC has an implied router (shown in the configuration diagram for this scenario.) For this scenario, the VPC wizard creates a route table that routes all traffic destined for an address outside the VPC to the Internet gateway, and associates this route table with the subnet. Otherwise, you'd need to create and associate the route table yourself.
The following table shows what the route table looks like for the example addresses used in the
configuration diagram for this scenario. The first row shows the entry for local routing in the VPC; this entry enables the instances in this VPC to communicate with each other.The second row shows the entry for routing all other subnet traffic to the Internet gateway, which is specified using its AWS-assigned identifier.
---------------------------------------------------------------------------------------------------------------------
19
AWS provides two features that you can use to increase security in your VPC: security groups and network ACLs. Both features enable you to control the inbound and outbound traffic for your instances, but security groups work at the instance level, while network ACLs work at the subnet level.
Security groups alone can meet the needs of many VPC users. However, some VPC users decide to use both security groups and network ACLs to take advantage of the additional layer of security that network ACLs provide.
Recommended Security Group Rules
Your VPC comes with a default security group whose initial settings allow all outbound traffic and allow all traffic between instances assigned to the security group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to the default security group for the VPC.
#20
By default, new security groups start with only an outbound rule that allows all traffic to leave the instances.You must add rules to enable any inbound traffic or to restrict the outbound traffic.
The default security group for a VPC has rules that automatically allow assigned instances to communicate with each other. To allow that type of communication between the instances in your VPC, you must add a rule like the following to your security groups.
#23
The instances in the public subnet can receive inbound traffic directly from the Internet, whereas the
instances in the private subnet can't. The instances in the public subnet can send outbound traffic directly to the Internet, whereas the instances in the private subnet can't. Instead, the instances in the private subnet can access the Internet by using a network address translation (NAT) gateway that resides in the public subnet. The database servers can connect to the Internet for software updates using the NAT gateway, but the Internet cannot initiate connections to the database servers.
Note
You can also use the VPC wizard to configure a VPC with a NAT instance; however, we
recommend that you use a NAT gateway. For more information, see NAT Gateways.
#24A NAT gateway with its own Elastic IP address. This enables instances in the private subnet to send
requests to the Internet (for example, for software updates)
A route table associated with the public subnet.This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the private subnet. The route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate with the Internet through the NAT gateway.
25#
Tip:
To help manage the instances in the private subnet, you can set up bastion servers in the public
subnet to act as proxies. For example, you can set up SSH port forwarders or RDP gateways
in the public subnet to proxy the traffic going to your database servers from your own network.
In this scenario, all traffic from each subnet that is bound for AWS (for example, to the Amazon EC2 or Amazon S3 endpoints) goes over the Internet gateway. The database servers in the private subnet can't receive traffic from the Internet directly because they don't have Elastic IP addresses. However, the database servers can send and receive Internet traffic through the NAT device in the public subnet.
Any additional subnets that you create use the main route table by default, which means that they are private subnets by default. If you'd like to make a subnet public, you can always change the route table that it's associated with.
26#
Your VPC comes with a default security group whose initial settings deny all inbound traffic, allow all outbound traffic, and allow all traffic between instances assigned to the group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to this default security group.
The instances assigned to a security group can be in different subnets.
30#
By default, instances launched into a nondefault VPC are not assigned a public IP address.
To be able to connect to your instance in the public subnet, you can assign a public IP address now,
or allocate an Elastic IP address and assign it to your instance after it's launched.To assign a publicIP address now, ensure that you choose Enable from the Auto-assign Public IP list.You do not
need to assign a public IP address to an instance in the private subnet.
Note
You can only assign a public IP address to a single, new network interface with the device
index of eth0. For more information, see Assigning a Public IP Address During Launch (p. 123).
31#
You will also require a security group for your NAT instance (NATSG), which allows the NAT instance to receive Internet-bound traffic from instances in the private subnet, as well as SSH traffic from your network. The NAT instance can also send traffic to the Internet, so that instances in the private subnet can get software updates.
33#
Scenario 3:VPC with Public and Private Subnets and Hardware VPN Access
The configuration for this scenario includes a virtual private cloud (VPC) with a public subnet and a private subnet, and a virtual private gateway to enable communication with your own network over an IPsec VPN tunnel.We recommend this scenario if you want to extend your network into the cloud and also directly access the Internet from your VPC. This scenario enables you to run a multi-tiered application with a scalable web front end in a public subnet, and to and to house your data in a private subnet that is connected to your network by an IPsec VPN connection.
34#
A VPN connection between your VPC and your network. The VPN connection consists of a virtual
private gateway located on the Amazon side of the VPN connection and a customer gateway located on your side of the VPN connection.
Instances with private IP addresses in the subnet range (examples: 10.0.0.5 and 10.0.1.5), which
enables the instances to communicate with each other and other instances in the VPC. Instances in the public subnet also have Elastic IP addresses (example: 198.51.100.1), which enables them to be
reached from the Internet. The instances can have public IP addresses assigned at launch instead of
Elastic IP addresses. Instances in the VPN-only subnet are back-end servers that don't need to accept incoming traffic from the Internet, but can send and receive traffic from your network.
A custom route table associated with the public subnet. This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the VPN-only subnet. The route table contains an entry that
enables instances in the subnet to communicate with other instances in the VPC, and an entry that
enables instances in the subnet to communicate directly with your network.
Subscribe to:
Comments (Atom)