** VPCNetworkAdminGuide **
Difference between Public IP and Static IP:
When you launch an EC2 instance, you recieve a Public IP address by which that instance is reachable.
Once you stop that instance and restart the you get a new Public IP for the same instance's.
So, Public IP get's changed everytime for an instance after stop/start.
To overcome with this problem, we attach an Elastic IP to an Instance which doesn't change after you stop / start the instance as many times.
Advantage of Having Elastic IP
-> It is kind of static IP for your Instance.
-> Doesn't change after stop/start.
If you have Elastic IP in your account and it's not in use, then you will be charged for it.
Ref: Vikash Jha
https://www.quora.com/Whats-the-difference-between-a-public-IP-and-an-elastic-IP-in-AWS-EC2
__________________
Internet Gateway :
Route Tables.
-----------------------------------
Route Table:
then we prioritize the routes as follows in your VPC, from most preferred to least preferred:
Difference between Public IP and Static IP:
When you launch an EC2 instance, you recieve a Public IP address by which that instance is reachable.
Once you stop that instance and restart the you get a new Public IP for the same instance's.
So, Public IP get's changed everytime for an instance after stop/start.
To overcome with this problem, we attach an Elastic IP to an Instance which doesn't change after you stop / start the instance as many times.
Advantage of Having Elastic IP
-> It is kind of static IP for your Instance.
-> Doesn't change after stop/start.
If you have Elastic IP in your account and it's not in use, then you will be charged for it.
Ref: Vikash Jha
https://www.quora.com/Whats-the-difference-between-a-public-IP-and-an-elastic-IP-in-AWS-EC2
__________________
Internet Gateway :
Route Tables.
-----------------------------------
Route Table:
then we prioritize the routes as follows in your VPC, from most preferred to least preferred:
- Local routes for the VPC
- Static routes whose targets are an Internet gateway, a virtual private gateway, a network interface, an instance ID, a VPC peering connection, or a VPC endpoint
- Any propagated routes from a VPN connection or AWS Direct Connect connection
If you have overlapping routes within a VPN connection and longest prefix match cannot be applied, then we prioritize the routes as follows in the VPN connection, from most preferred to least preferred:
- BGP propagated routes from an AWS Direct Connect connection
- Manually added static routes for a VPN connection
- BGP propagated routes from a VPN connection
Note
When you use the wizard in the console to create a VPC with a gateway, the wizard automatically updates the route tables to use the gateway. If you're using the command line tools or API to set up your VPC, you must update the route tables yourself.
=================================================
________________________________________________________________________
7
A main route table that all VPCs have by default, and a custom route table that was created by the wizard. The custom route table is associated with your subnet, which means that the routes in that table determine how the traffic for the subnet flows.If you add a new subnet to your VPC, it uses the main route table by default.
11
A security group acts as a virtual firewall to control the traffic for its associated instances.To use a security group, you add the inbound rules to control incoming traffic to the instance, and outbound rules to control the outgoing traffic from your instance. To associate a security group with an instance, you specify the security group when you launch the instance. If you add and remove rules from the security group, we apply those changes to the instances associated with the security group automatically.
Your VPC comes with a default security group. Any instance not associated with another security group during launch is associated with the default security group.
14
A public subnet — a subnet that has a route to an Internet gateway. However, the instance in your subnet also needs a public IP address to be able to communicate with the Internet. By default, an instance in a nondefault VPC is not assigned a public IP address.
18,19
An Internet gateway. This connects the VPC to the Internet and to other AWS products.
An instance with a private IP address in the subnet range (example: 10.0.0.6), which enables the
instance to communicate with other instances in the VPC, and an Elastic IP address (example:
198.51.100.2), which enables the instance to be reached from the Internet.
A route table entry that enables instances in the subnet to communicate with other instances in the VPC, and a route table entry that enables instances in the subnet to communicate directly over the Internet.
Tip
If you'd like instances in your VPC to communicate over the Internet without having to assign
each instance an Elastic IP address, you can use a NAT gateway.
Your VPC has an implied router (shown in the configuration diagram for this scenario.) For this scenario, the VPC wizard creates a route table that routes all traffic destined for an address outside the VPC to the Internet gateway, and associates this route table with the subnet. Otherwise, you'd need to create and associate the route table yourself.
The following table shows what the route table looks like for the example addresses used in the
configuration diagram for this scenario. The first row shows the entry for local routing in the VPC; this entry enables the instances in this VPC to communicate with each other.The second row shows the entry for routing all other subnet traffic to the Internet gateway, which is specified using its AWS-assigned identifier.
---------------------------------------------------------------------------------------------------------------------
19
AWS provides two features that you can use to increase security in your VPC: security groups and network ACLs. Both features enable you to control the inbound and outbound traffic for your instances, but security groups work at the instance level, while network ACLs work at the subnet level.
Security groups alone can meet the needs of many VPC users. However, some VPC users decide to use both security groups and network ACLs to take advantage of the additional layer of security that network ACLs provide.
Recommended Security Group Rules
Your VPC comes with a default security group whose initial settings allow all outbound traffic and allow all traffic between instances assigned to the security group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to the default security group for the VPC.
#20
By default, new security groups start with only an outbound rule that allows all traffic to leave the instances.You must add rules to enable any inbound traffic or to restrict the outbound traffic.
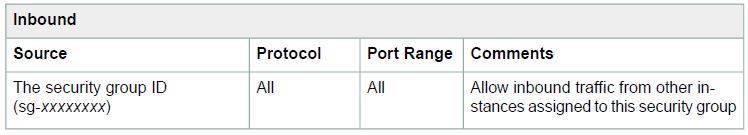
The default security group for a VPC has rules that automatically allow assigned instances to communicate with each other. To allow that type of communication between the instances in your VPC, you must add a rule like the following to your security groups.
#23
The instances in the public subnet can receive inbound traffic directly from the Internet, whereas the
instances in the private subnet can't. The instances in the public subnet can send outbound traffic directly to the Internet, whereas the instances in the private subnet can't. Instead, the instances in the private subnet can access the Internet by using a network address translation (NAT) gateway that resides in the public subnet. The database servers can connect to the Internet for software updates using the NAT gateway, but the Internet cannot initiate connections to the database servers.
Note
You can also use the VPC wizard to configure a VPC with a NAT instance; however, we
recommend that you use a NAT gateway. For more information, see NAT Gateways.
#24A NAT gateway with its own Elastic IP address. This enables instances in the private subnet to send
requests to the Internet (for example, for software updates)
A route table associated with the public subnet.This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the private subnet. The route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate with the Internet through the NAT gateway.
25#
Tip:
To help manage the instances in the private subnet, you can set up bastion servers in the public
subnet to act as proxies. For example, you can set up SSH port forwarders or RDP gateways
in the public subnet to proxy the traffic going to your database servers from your own network.
In this scenario, all traffic from each subnet that is bound for AWS (for example, to the Amazon EC2 or Amazon S3 endpoints) goes over the Internet gateway. The database servers in the private subnet can't receive traffic from the Internet directly because they don't have Elastic IP addresses. However, the database servers can send and receive Internet traffic through the NAT device in the public subnet.
Any additional subnets that you create use the main route table by default, which means that they are private subnets by default. If you'd like to make a subnet public, you can always change the route table that it's associated with.
26#
Your VPC comes with a default security group whose initial settings deny all inbound traffic, allow all outbound traffic, and allow all traffic between instances assigned to the group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to this default security group.
The instances assigned to a security group can be in different subnets.
30#
By default, instances launched into a nondefault VPC are not assigned a public IP address.
To be able to connect to your instance in the public subnet, you can assign a public IP address now,
or allocate an Elastic IP address and assign it to your instance after it's launched.To assign a publicIP address now, ensure that you choose Enable from the Auto-assign Public IP list.You do not
need to assign a public IP address to an instance in the private subnet.
Note
You can only assign a public IP address to a single, new network interface with the device
index of eth0. For more information, see Assigning a Public IP Address During Launch (p. 123).
31#
You will also require a security group for your NAT instance (NATSG), which allows the NAT instance to receive Internet-bound traffic from instances in the private subnet, as well as SSH traffic from your network. The NAT instance can also send traffic to the Internet, so that instances in the private subnet can get software updates.
33#
Scenario 3:VPC with Public and Private Subnets and Hardware VPN Access
The configuration for this scenario includes a virtual private cloud (VPC) with a public subnet and a private subnet, and a virtual private gateway to enable communication with your own network over an IPsec VPN tunnel.We recommend this scenario if you want to extend your network into the cloud and also directly access the Internet from your VPC. This scenario enables you to run a multi-tiered application with a scalable web front end in a public subnet, and to and to house your data in a private subnet that is connected to your network by an IPsec VPN connection.
34#
A VPN connection between your VPC and your network. The VPN connection consists of a virtual
private gateway located on the Amazon side of the VPN connection and a customer gateway located on your side of the VPN connection.
Instances with private IP addresses in the subnet range (examples: 10.0.0.5 and 10.0.1.5), which
enables the instances to communicate with each other and other instances in the VPC. Instances in the public subnet also have Elastic IP addresses (example: 198.51.100.1), which enables them to be
reached from the Internet. The instances can have public IP addresses assigned at launch instead of
Elastic IP addresses. Instances in the VPN-only subnet are back-end servers that don't need to accept incoming traffic from the Internet, but can send and receive traffic from your network.
A custom route table associated with the public subnet. This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the VPN-only subnet. The route table contains an entry that
enables instances in the subnet to communicate with other instances in the VPC, and an entry that
enables instances in the subnet to communicate directly with your network.
=================================================
________________________________________________________________________
7
A main route table that all VPCs have by default, and a custom route table that was created by the wizard. The custom route table is associated with your subnet, which means that the routes in that table determine how the traffic for the subnet flows.If you add a new subnet to your VPC, it uses the main route table by default.
11
A security group acts as a virtual firewall to control the traffic for its associated instances.To use a security group, you add the inbound rules to control incoming traffic to the instance, and outbound rules to control the outgoing traffic from your instance. To associate a security group with an instance, you specify the security group when you launch the instance. If you add and remove rules from the security group, we apply those changes to the instances associated with the security group automatically.
Your VPC comes with a default security group. Any instance not associated with another security group during launch is associated with the default security group.
14
A public subnet — a subnet that has a route to an Internet gateway. However, the instance in your subnet also needs a public IP address to be able to communicate with the Internet. By default, an instance in a nondefault VPC is not assigned a public IP address.
18,19
An Internet gateway. This connects the VPC to the Internet and to other AWS products.
An instance with a private IP address in the subnet range (example: 10.0.0.6), which enables the
instance to communicate with other instances in the VPC, and an Elastic IP address (example:
198.51.100.2), which enables the instance to be reached from the Internet.
A route table entry that enables instances in the subnet to communicate with other instances in the VPC, and a route table entry that enables instances in the subnet to communicate directly over the Internet.
Tip
If you'd like instances in your VPC to communicate over the Internet without having to assign
each instance an Elastic IP address, you can use a NAT gateway.
Your VPC has an implied router (shown in the configuration diagram for this scenario.) For this scenario, the VPC wizard creates a route table that routes all traffic destined for an address outside the VPC to the Internet gateway, and associates this route table with the subnet. Otherwise, you'd need to create and associate the route table yourself.
The following table shows what the route table looks like for the example addresses used in the
configuration diagram for this scenario. The first row shows the entry for local routing in the VPC; this entry enables the instances in this VPC to communicate with each other.The second row shows the entry for routing all other subnet traffic to the Internet gateway, which is specified using its AWS-assigned identifier.
---------------------------------------------------------------------------------------------------------------------
19
AWS provides two features that you can use to increase security in your VPC: security groups and network ACLs. Both features enable you to control the inbound and outbound traffic for your instances, but security groups work at the instance level, while network ACLs work at the subnet level.
Security groups alone can meet the needs of many VPC users. However, some VPC users decide to use both security groups and network ACLs to take advantage of the additional layer of security that network ACLs provide.
Recommended Security Group Rules
Your VPC comes with a default security group whose initial settings allow all outbound traffic and allow all traffic between instances assigned to the security group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to the default security group for the VPC.
#20
By default, new security groups start with only an outbound rule that allows all traffic to leave the instances.You must add rules to enable any inbound traffic or to restrict the outbound traffic.
The default security group for a VPC has rules that automatically allow assigned instances to communicate with each other. To allow that type of communication between the instances in your VPC, you must add a rule like the following to your security groups.
#23
The instances in the public subnet can receive inbound traffic directly from the Internet, whereas the
instances in the private subnet can't. The instances in the public subnet can send outbound traffic directly to the Internet, whereas the instances in the private subnet can't. Instead, the instances in the private subnet can access the Internet by using a network address translation (NAT) gateway that resides in the public subnet. The database servers can connect to the Internet for software updates using the NAT gateway, but the Internet cannot initiate connections to the database servers.
Note
You can also use the VPC wizard to configure a VPC with a NAT instance; however, we
recommend that you use a NAT gateway. For more information, see NAT Gateways.
#24A NAT gateway with its own Elastic IP address. This enables instances in the private subnet to send
requests to the Internet (for example, for software updates)
A route table associated with the public subnet.This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the private subnet. The route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate with the Internet through the NAT gateway.
25#
Tip:
To help manage the instances in the private subnet, you can set up bastion servers in the public
subnet to act as proxies. For example, you can set up SSH port forwarders or RDP gateways
in the public subnet to proxy the traffic going to your database servers from your own network.
In this scenario, all traffic from each subnet that is bound for AWS (for example, to the Amazon EC2 or Amazon S3 endpoints) goes over the Internet gateway. The database servers in the private subnet can't receive traffic from the Internet directly because they don't have Elastic IP addresses. However, the database servers can send and receive Internet traffic through the NAT device in the public subnet.
Any additional subnets that you create use the main route table by default, which means that they are private subnets by default. If you'd like to make a subnet public, you can always change the route table that it's associated with.
26#
Your VPC comes with a default security group whose initial settings deny all inbound traffic, allow all outbound traffic, and allow all traffic between instances assigned to the group. If you don't specify a security group when you launch an instance, the instance is automatically assigned to this default security group.
The instances assigned to a security group can be in different subnets.
30#
By default, instances launched into a nondefault VPC are not assigned a public IP address.
To be able to connect to your instance in the public subnet, you can assign a public IP address now,
or allocate an Elastic IP address and assign it to your instance after it's launched.To assign a publicIP address now, ensure that you choose Enable from the Auto-assign Public IP list.You do not
need to assign a public IP address to an instance in the private subnet.
Note
You can only assign a public IP address to a single, new network interface with the device
index of eth0. For more information, see Assigning a Public IP Address During Launch (p. 123).
31#
You will also require a security group for your NAT instance (NATSG), which allows the NAT instance to receive Internet-bound traffic from instances in the private subnet, as well as SSH traffic from your network. The NAT instance can also send traffic to the Internet, so that instances in the private subnet can get software updates.
33#
Scenario 3:VPC with Public and Private Subnets and Hardware VPN Access
The configuration for this scenario includes a virtual private cloud (VPC) with a public subnet and a private subnet, and a virtual private gateway to enable communication with your own network over an IPsec VPN tunnel.We recommend this scenario if you want to extend your network into the cloud and also directly access the Internet from your VPC. This scenario enables you to run a multi-tiered application with a scalable web front end in a public subnet, and to and to house your data in a private subnet that is connected to your network by an IPsec VPN connection.
34#
A VPN connection between your VPC and your network. The VPN connection consists of a virtual
private gateway located on the Amazon side of the VPN connection and a customer gateway located on your side of the VPN connection.
Instances with private IP addresses in the subnet range (examples: 10.0.0.5 and 10.0.1.5), which
enables the instances to communicate with each other and other instances in the VPC. Instances in the public subnet also have Elastic IP addresses (example: 198.51.100.1), which enables them to be
reached from the Internet. The instances can have public IP addresses assigned at launch instead of
Elastic IP addresses. Instances in the VPN-only subnet are back-end servers that don't need to accept incoming traffic from the Internet, but can send and receive traffic from your network.
A custom route table associated with the public subnet. This route table contains an entry that enables instances in the subnet to communicate with other instances in the VPC, and an entry that enables instances in the subnet to communicate directly with the Internet.
The main route table associated with the VPN-only subnet. The route table contains an entry that
enables instances in the subnet to communicate with other instances in the VPC, and an entry that
enables instances in the subnet to communicate directly with your network.


No comments:
Post a Comment